
The Impacts of AI on Application Security Testing
As technology continues to evolve at an unprecedented pace, the landscape of application testing is constantly on the edge of ...

As technology continues to evolve at an unprecedented pace, the landscape of application testing is constantly on the edge of ...

The choice of using ASP.NET is growing, especially in legacy programs, as it offers a reliable, secure, and well-supported pla...

As ActionScript becomes an essential language for application development, developers must become aware of the security considerations th...

The last few years have seen South American (LATAM) countries become a hub for technology startups and established organizatio...

For the past several decades, businesses and governmental agencies have been using the COBOL programming language for numerous...

ABAP (Advanced Business Application Programming), the high-level programming language created by the software company SAP SE, ...

Software security involves more than passwords, access control, and social engineering. Even if a company implements these sec...

The Java programming language is versatile and powerful. It can be used in a wide variety of settings to allow developers to create robus...

For developers, it is essential to implement security with the language’s risk at hand. Kotlin is no different and presents a myria...
The EU’s relatively new Cybersecurity Strategy unveiled in 2020 had always been meant to improve cyber resilience in the region, but a ...

For developers, it is essential to implement security with the language’s risk at hand. Golang is no different and presents a myria...

Do you want to learn about the wide variety of vulnerabilities and weak points that you need to be aware of when developing in JavaScript...

On April 4, 2022, the State Department formed a new bureau — the Bureau of Cybersecurity and Digital
Secure Your APIs With Kiuwan SAST
Gartner estimates that APIs will soon become the most commonly targeted vulnerability within org...
A security footprint is the sum of a digital item’s security requirements. A program’s security footprint would include all t...

Developing applications comes with considerable security risk. With the expansion of IoT devices and the ever-growing reliance on applica...

Is your development team feeling squeezed between the pressure to deliver fast, and the need to test for defects and security vulnerabili...

This ebook will present an in-depth examination of the wide range of risks that challenge software developers. You’ll also get prac...

Leverage the power of Kiuwan code security within your continuous integration process using Travis CI.
During this webinar, we out...

In this guide for 2022, the Kiuwan security team gives developers key recommendations and best practices for ensuring secure application ...

Safeguarding your code and protecting against vulnerabilities are top priorities. You understand the criticality of identifying security ...

Vulnerabilities in your code are exposing applications to risk from attackers, and with the ever expanding cybersecurity surface, the cha...

Modern organizations run software from a myriad of sources, including third-party applications which have a variety of original sources. ...

Modern organizations run software from a myriad of sources, including third-party applications which have a variety of original sources. ...

Businesses need a framework that enables them to identify, quantify, respond to, and mitigate risks to their digital infrastructure and a...

Application security is an essential facet for businesses, especially those thatwork with personal data. In this webinar the Kiuwan team ...
Cybersecurity risks are commonplace for businesses across sectors, but over the past 18 months cyberthreats have become increasingly prev...

Using the Kiuwan API – an introduction to connecting to a Kiuwan account via API to pull back data and start to integrate Kiuwan into y...

A webinar for developers, QA personnel, information security specialists from frontline to managers, with any level of security testing e...

Learn about the particular security threats your applications are exposed to when developing in the ABAP language. Get in-depth insight i...

Securing your business in today’s digital world goes beyond the surface; it involves a deep dive into the world of application secu...

Development security can be a bottleneck for a high-velocity DevOps process. By adding security throughout your development cycle, you ca...

This complete guide provides an overview of the extensive range of vulnerabilities outlined in the OWASP Top 10 for 2021. This guide also...

Learn how to avoid security issues that exist within the REST API. This guide provides an overview on the main security problems that nee...
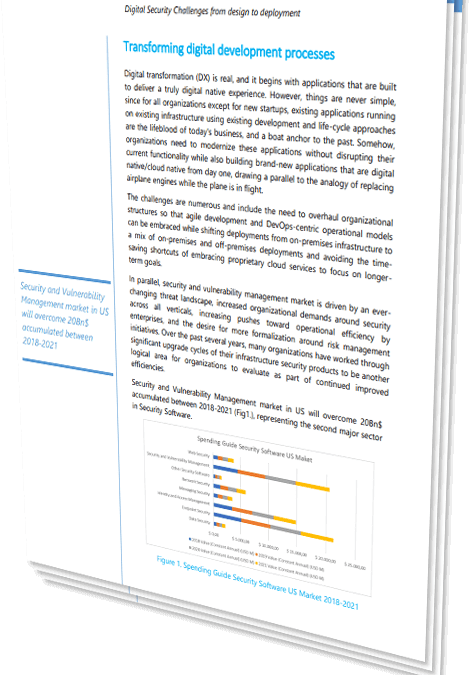
The Secure Software Development Life Cycle (SSDLC) promotes the mindset that everyone is responsible for security. Organizations that fol...

Injection attacks pose a significant threat to businesses worldwide. These are not only confined to one type but span across various form...

Are you looking for a total overview of the risks associated with cross-site request forgery? This comprehensive ebook provides enlighten...
In this webinar, you’ll learn how to run automatic code security audits by triggering Kiuwan scans in your build definitions. The Kiuwa...

Kiuwan enables a true shift-left approach to security in DevOps through its integration with the Eclipse IDE. Developers can analyze sour...

Kiuwan enables a true shift-left approach to security in DevOps through its integration with Microsoft Visual Studio. Developers can an...

There’s a lot you need to know about your application. What critical defects exist, and how much time will your team need to repair the...
Join us for an insightful webinar that delves into how Kiuwan can be fully integrated within the Assembla software development platform. ...
Nearly every developer working on software projects will use at some point open-source elements in their code. But many are unaware that ...

This webinar is all about Kiuwan Life Cycle, the Kiuwan module created to put you in full control of your application’s deliveries from...